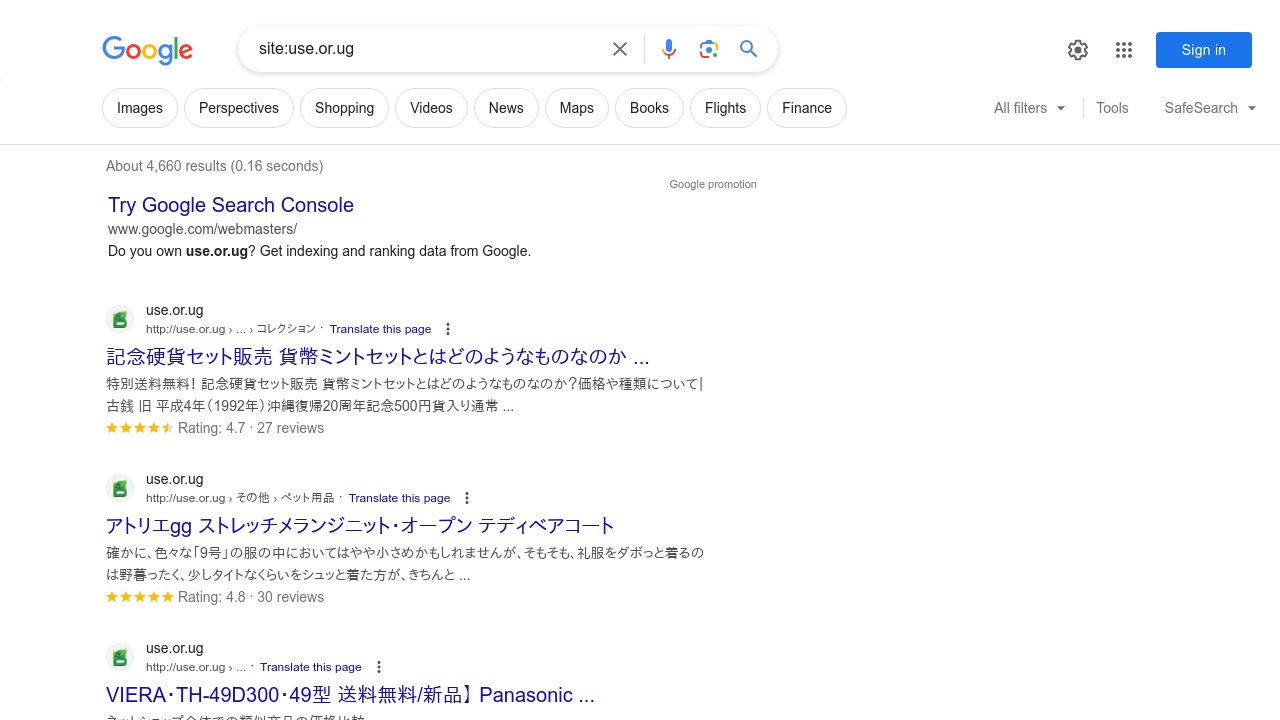
The fourth result of a Google search for ‘Uganda Securities Exchange,’ until about a week ago, had Japanese content in the description, consistent with a Japanese keyword hack. But at least it had the USE website icon. This is no longer the case.
The same search today shows that the first result from the USE website is only third in the results, a red flag for a website of its profile. In fourth place, also from the USE, is a PDF document entitled ‘USE Listing Profile.’ However, the name of the site is not displayed above the URL as it should be, but ‘AQUACLEAN’, and the favicon next to the results page is not the USE favicon.
The spam – the Japanese characters, Aquaclean, and the unrelated icon — is the result of hacks known by different names depending on the content produced. These include Japanese keyword/SEO hack, pharma SEO spam, Chinese hack, among others. Hackers inject malicious code into website files, creating spam content in page titles and descriptions. The code also creates entirely new spam pages hidden in randomly created directories. The spam pages are monetised by redirecting users to counterfeit online stores.
The hackers’ intention is to get their spam ranked in search engines by piggybacking on the target site’s resources and reputation. This means that existing content is displayed to visitors as it should be, while search engines see something different.
The hackers of the USE website created spammy pages and then some. When ran our search Tuesday, we found only three results from its domain on the first page of Google results — the two mentioned above and another link to a PDF file. To see more, we used Google’s feature that only returns results from a specific domain.
All the results we saw were spam pages. We scrolled down the results page for a while, but nothing relevant – nothing that was not spam – came up. When we clicked on the first hyperlink, we got an error message saying that the page was unavailable. Fortunately, we were able to retrieve the cached version of the page, which showed the original content before it was deleted.
The page, cached by Google on 22 October, was a Japanese language store for shower equipment. All links on the page are to similar spam pages hosted on the USE site, which have since been removed, while the outbound links are inactive due to browser restrictions on fetching scripts hosted on other sites (scripts cached by Google but hosted on the USE site).
(You can see the archived version of the cached page here, in case the link in the previous paragraph has been cleared from Google’s cache.)
There could be several reasons why USE’s own pages – for example, the home page or the listing rules page – do not appear in the search results we have found. One is that Google (and other search engines, although we haven’t checked them) may be penalising the site. The other reason, which is related to the first, is that they have simply not seen these pages in recent crawls of the site and have pushed them down in their list of results.
At last check, the malware inserted by the hackers presents different content depending on the user agent of the visitor. The majority of visitors see the real content — what the USE wants you to see — while Google’s crawlers or bots see completely different material.
Typing the URL of the USE homepage into Google’s rich results test page – a Google site that tests web pages and shows the rich results that can be generated from their structured data – does not reveal the USE homepage visible to human visitors, but rather a flashy page like those found on casino websites. (To view the page, click view tested page after the results are returned and click on screenshot; you can also copy the html and paste it into an online html viewer. This is what it looks like.)
The (meta) description of the page – “Instafury adalah website kumpulan link situs toto togel dan toto slot terpercaya 2023 dengan berlisensi resmi di indonesia” – is in Indonesian. In English, according to Google Translate, it means: “Instafury is a website that collects links to trusted lottery and toto slot sites for 2023 with an official licence in Indonesia.”
Every time Google crawls the USE homepage, it is redirected to the Instafury page – that is what it adds to its index. What human visitors find is one thing, but what search engines index is quite another.
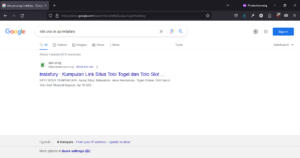
A quick way to prove this is to search the USE website for “instafury.” The link returned by Google is, well, the USE homepage (click on image to expand). When we tried to access the cached version of the result page shown by Google, we found that it had been redirected to, and had cached the “lottery and toto slot sites” page.
We randomly selected other pages and ran them through the rich results test page: the result – Instafury. These include the listing rules page, SCD forms and the disclaimer page. It is therefore safe to conclude that all pages on the site are redirecting search engines to spam pages when crawled.
USE surely has someone responsible for identifying and dealing with such problems, and we believe they must be aware of this given how long it has been going on. We ran the site through an online malware scanner and it showed that it had been scanned a month ago, leading us to believe that someone at the exchange had done it. However, the scan found no problems, which is undoubtedly false.
Protecting against such threats does not require a lot of resources, nor is it a difficult undertaking. So if the Uganda Securities Exchange seems at a loss as to what to do, what other data are they not adequately protecting?






